- Which of the following methods are used to pass any number of parameters to the operating system through system calls?
(1) Registers              (2) Block or table in main memory
(3) Stack                    (4) Block in main memory and stack
Answer: 4
- Match the Agile Process models with the task performed during the model:
List-I                                                       List-II
(a) Scrum                                                (i) CRC cards
(b) Adaptive software development           (ii) Sprint backlog
(c) Extreme programming                         (iii) <action> the <result> <by/for/of/to> a(n)
<object>
(d) Feature-driven development                (iv) Time box release plan
Choose the correct option from those given below:
(1) (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii)               (2) (a)-(i), (b)-(iii), (c)-(ii), (d)-(iv)
(3) (a)-(ii), (b)-(i), (c)-(iv), (d)-(iii)               (4) (a)-(i), (b)-(iv), (c)-(ii), (d)-(iii)
Answer: 1
- Match List-I and List-II:
List-I                                   List-II
(a) Physical layer                  (i) Provide token management service
(b) Transport layer               (ii) Concerned with transmitting raw bits over a
communication channel
(c) Session layer                  (iii) Concerned with the syntax and semantics of the
information transmitted
(d) Presentation layer           (iv) True end-to-end layer from source to destination
Choose the correct option from those given below:
(1) (a)-(ii), (b)-(iv), (c)-(iii), (d)-(i)               (2) (a)-(iv), (b)-(iii), (c)-(ii), (d)-(i)
(3) (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii)               (4) (a)-(iv), (b)-(ii), (c)-(i), (d)-(iii)
Answer: 3
- According to Dempster-Shafer theory for uncertainty management,
(1) Bel(A) + Bel(¬A)≤1                              (2) Bel(A) + Bel(¬A)≥1
(3) Bel(A) + Bel(¬A)=1                    (4) Bel(A) + Bel(¬A)=0
Where Bel(A) denotes Belief of event A.
Answer: 1
- Consider the following grammars:
G1: S→aSb | bSa | aa
G2: S→aSb | bSa | SS | λ
G3: S→aSb | bSa | SS | a
G4: S→aSb | bSa | SS | SSS | λ
Which of the following is correct w.r.t. the above grammars?
(1) G1 and G3 are equivalent           (2) G2 and G3 are equivalent
(3) G2 and G4 are equivalent           (4) G3 and G4 are equivalent
Answer: 3
- Consider the following:
(a) Trapping at local maxima
(b) Reaching a plateau
(c) Traversal along the ridge.
Which of the following option represents shortcomings of the hill climbing algorithm?
(1) (a) and (b) only               (2) (a) and (c) only
(3) (b) and (c) only               (4) (a), (b) and (c)
Answer: 4
- Consider the following statements with respect to the language L = {anbn | n ≥ 0}

Which one of the following is correct?
(1) only S1 and S2               (2) only S1 and S3
(3) only S2 and S3               (4) S1, S2 and S3
Answer: 4
- According to the ISO-9126 Standard Quality Model, match the attributes given in List-I with their definitions in List-II:
List-I                                   List-II
(a) Functionality                   (i) Relationship between level of performance and amount
of resources
(b) Reliability                        (ii) Characteristics related with achievement of purpose
(c) Efficiency                        (iii) Effort needed to make for improvement
(d) Maintainability                 (iv) Capability of software to maintain performance of
software
Choose the correct option from the ones given below:
(1) (a)-(i), (b)-(ii), (c)-(iii), (d)-(iv)               (2) (a)-(ii), (b)-(i), (c)-(iv), (d)-(iii)
(3) (a)-(ii), (b)-(iv), (c)-(i), (d)-(iii)               (4) (a)-(i), (b)-(ii), (c)-(iv), (d)-(iii)
Answer: 3
- Consider the following statements:
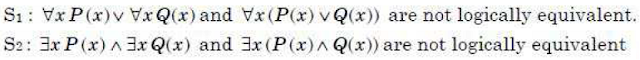
Which of the following statements is/are correct?
(1) Only S1                          (2) Only S2
(3) Both S1 and S2               (4) Neither S1 nor S2
Answer: 3
- Which of the following binary codes for decimal digits are self-complementing?
(a) 8421 code                      (b) 2421 code
(c) excess-3 code                 (d) excess-3 gray code
Choose the correct option:
(1) (a) and (b)            (2) (b) and (c)
(3) (c) and (d)            (4) (d) and (a)
Answer: 2
- How many reflexive relations are there on a set with 4 elements?
(1) 24                         (2) 212                               (3) 42                      (4) 2
Answer: 2
- Which of the following is not needed by an encryption algorithm used in Cryptography?
(1) KEY                     (2) Message
(3) Ciphertext             (4) User details
Answer: 3, 4
- Which of the component module of DBMS does rearrangement and possible ordering of operations, eliminate redundancy in query and use efficient algorithms and indexes during the execution of a query?
(1) query compiler                          (2) query optimizer
(3) Stored data manager                (4) Database processor
Answer: 2
- Consider a weighted directed graph. The current shortest distance from source S to node x is represented by d[x]. Let d[v] = 29, d[u] = 15, w[u, v] = 12. What is the updated value of d[v] based on current information
(1) 29              (2) 27           (3) 25           (4) 17
Answer: 2
- A rectangle is bounded by the lines x = 0; y = 0, x = 5 and y = 3. The line segment joining (–1, 0) and (4, 5), if clipped against this window will connect the points …………..
(1) (0, 1) and (3, 3)              (2) (0, 1) and (2, 3)
(3) (0, 1) and (4, 5)              (4) (0, 1) and (3, 5)
Answer: 2
- The following program is stored in the memory unit of the basic computer. Give the content of accumulator register in hexadecimal after the execution of the program.
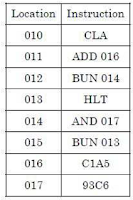
(1) A1B4                    (2) 81B4
(3) A184                    (4) 8184
Answer: 4
- Let a2c mod n = (ac)2 mod n and a2c+1 mod n = a.(ac)2 mod n. For a=7, b=17 and n=561, what is the value of ab(mod n)?
(1) 160            (2) 166                   (3) 157                   (4) 67
Answer: 1
- The order of schema?10?101? and ???0??1 are …………. and ………….. respectively.
(1) 5, 3                      (2) 5, 2                   (3) 7, 5                   (4) 8, 7
Answer: 2
- Consider the following statements:
S1: These exists no algorithm for deciding if any two Turning machine M1 and M2 accept
the same language.
S2: Let M1 and M2 be arbitrary Turing machines. The problem to determine
L(M1)ΓèåL(M2)is undecidable.
Which of the statements is (are) correct?
(1) Only S1                          (2) Only S2
(3) Both S1 and S2               (4) Neither S1 nor S1
Answer: 3
- Find minimum number of tables required for converting the following entity relationship diagram into relational database?
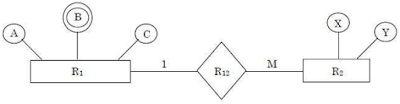
(1) 2                (2) 4             (3) 3             (4) 5
Answer: 3
